Installing a TMG Enterprise Management Server and Migrating and Existing Standalone Array: Part 1
 This is my current scenario: there are two existing servers in a stand-alone array - TMG01 and TMG02, and over in a DR site there is a new server (TMG03) that is in the process of being built. To comply with DR, all 3 servers must have their configurations up to date, however there is no direct communication allowed between the two DMZs, so simply adding to the new server as an array member is not possible.
This is my current scenario: there are two existing servers in a stand-alone array - TMG01 and TMG02, and over in a DR site there is a new server (TMG03) that is in the process of being built. To comply with DR, all 3 servers must have their configurations up to date, however there is no direct communication allowed between the two DMZs, so simply adding to the new server as an array member is not possible.
Fortunately, IPSec is allowed between each DMZ and the management DMZ so the plan is to configure IPSec between a new Enterprise Management Server in the Management DMZ (we"ll call it EMS01) and each of the three TMG servers.
Configuring the IPSec connection
There’s nothing fancy about this, just a plain ol’ IPSec setup:
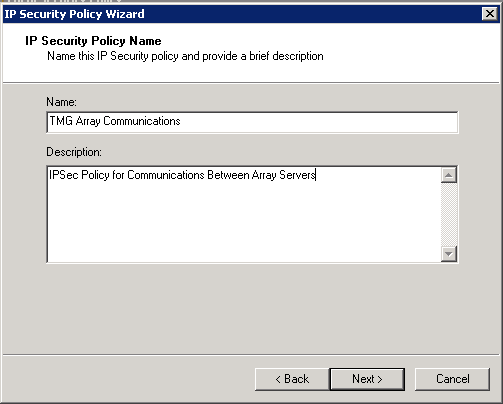
Create a new IPSec Policy using the wizard
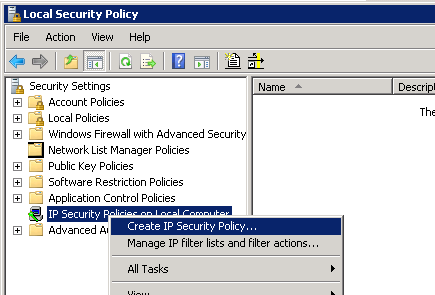
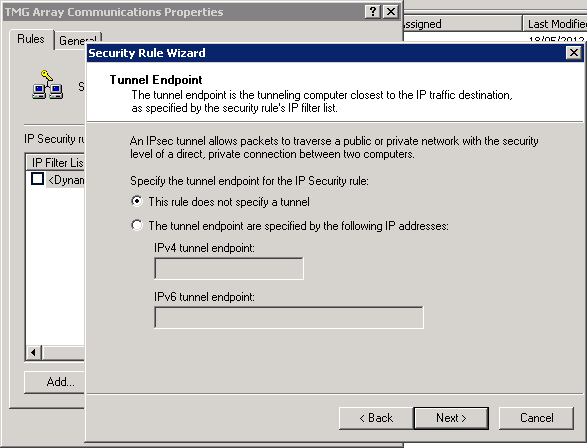
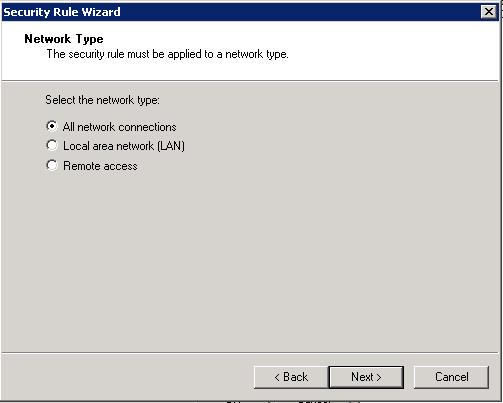
The policy does not specify a tunnel (it’s host-to-host) and we can keep it set to all network connections
Add an IP Filter list and name it accordingly - click Add to start the IP Filter Wizard and create an entry description from EMS01 to TMG01 - ensure the Mirrored option is checked.
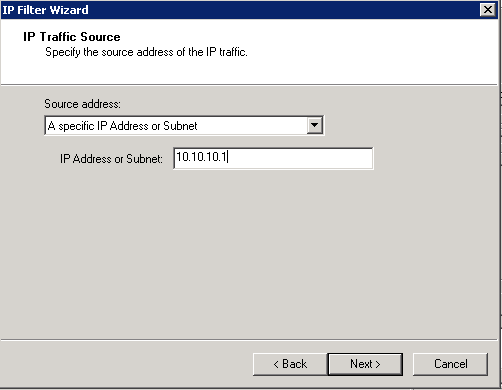
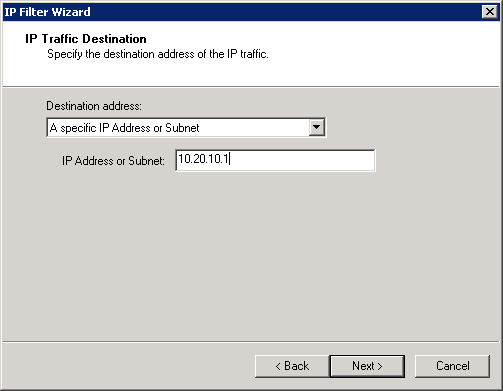
Add the IP address of EMS01 as the source, and TMG01 as the destination
We want to encrypt any traffic between these servers, and finish the wizard. Repeat this process (using the IP Filter Wizard) to add entries for all of the servers you wish to secure communications between. I created three rules, “EMS01 to TMG01”, “EMS01 to TMG02” and “EMS01 to TMG03”. Ensure the filter just created is selected and click Next.
Create a filter using the Filter Action wizard, named appropriately and set to negotiate security
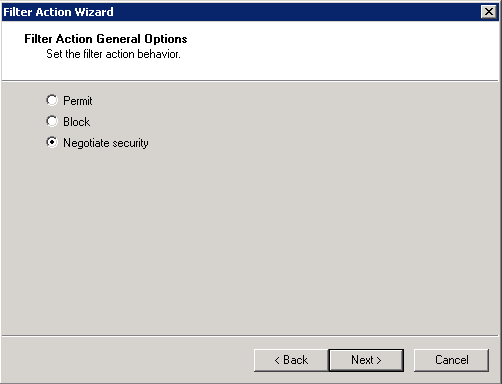
Deny unsecured communication and require the Integrity and encryption option.
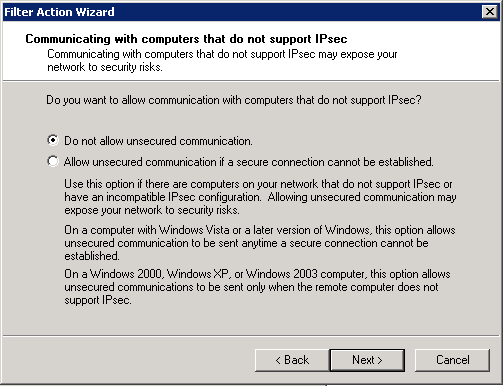
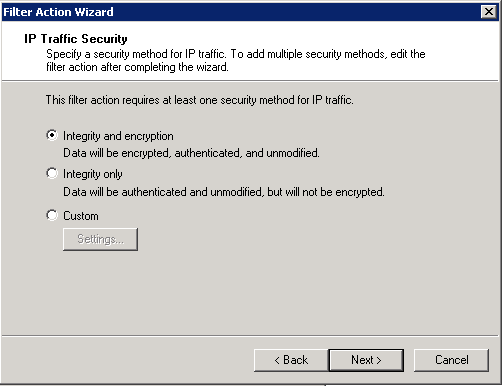
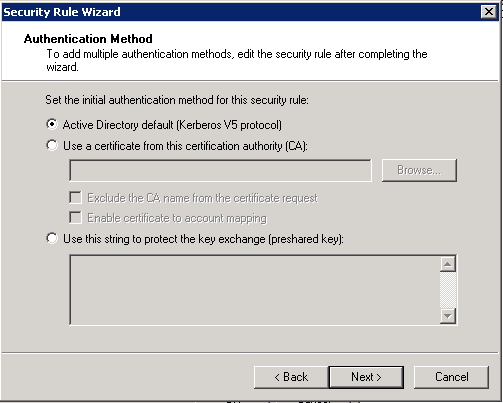
As all servers are domain members we can use Kerberos authentication. Finish the wizards
.
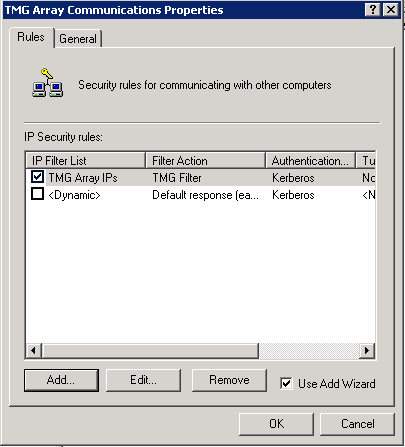
With the policy now created but unassigned, right click “IP Security Policies on Local Computer” and select “All Tasks > Export Policies…”. Copy the created .ipsec file to the other servers in the array and import the file.
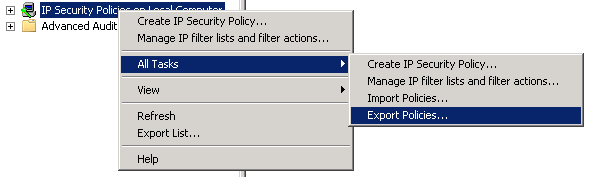
Add the new TMG EMS server to the Array Servers group within the existing TMG array and create a new rule allowing IPSec (add “IKE Client” and “IPSec ESP”) from and to “Array Servers” and “localhost” - this is critical as without it, we will not be able to communicate between these servers.
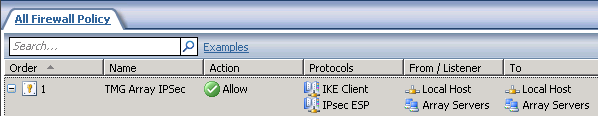
Finally, we are ready to “Assign” the IPSec policies on all TMG servers - I assigned it on EMS01 and TMG01 first and fired a ping to check the IPSec communication was working.
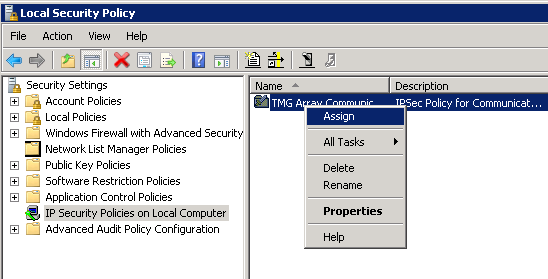
Troubleshooting note: you can add “IP Security Monitor” snap-in to an MMC console to monitor the IPSec communication.
Installing the TMG Enterprise Management Server
Run the Preparation Tool, selecting the Enterprise Management Server option and ensure all the pre-requisites are installed.

Accept the EULA and enter your license and company details. Set the installation path and then select the option to Create a new enterprise configuration.
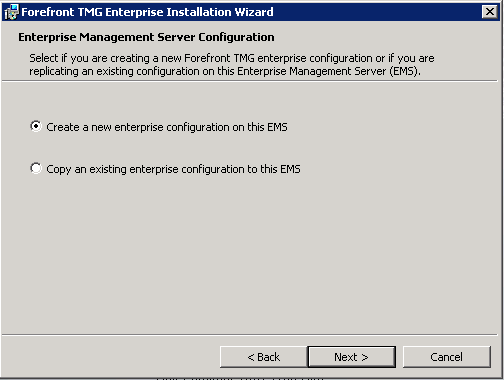
Enter a name and description for the Enterprise
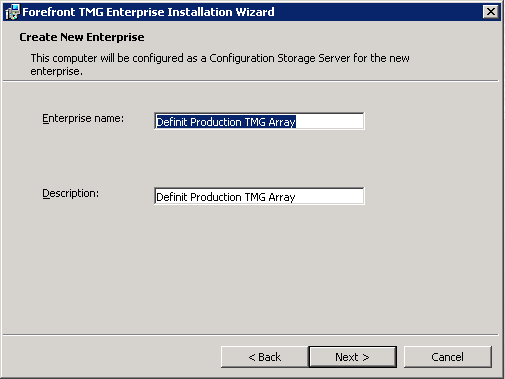
Since all my TMG servers are in a single domain, I will chose the Single Domain Deployment.
Hit install and watch the blue bar until completion
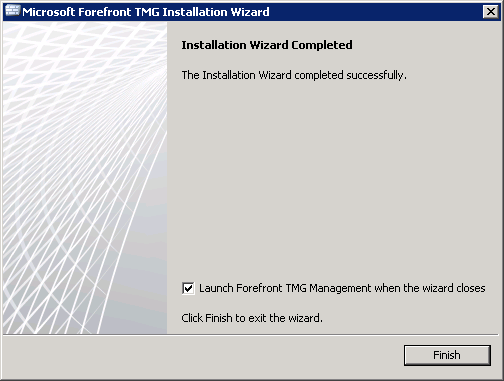
Firing up the console you can see the Enterprise configuration and Arrays.
Log on to the TMG stand-alone array and export the configuration to file.
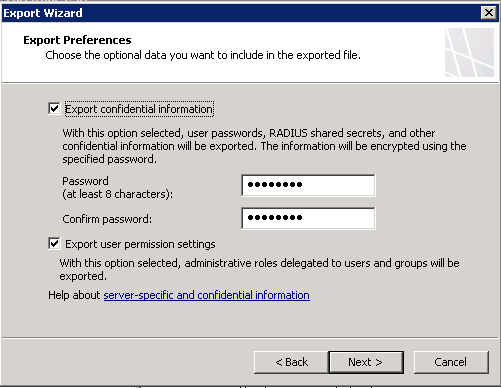
Run through the Export Wizard, ensuring that you export the confidential information and password protect it
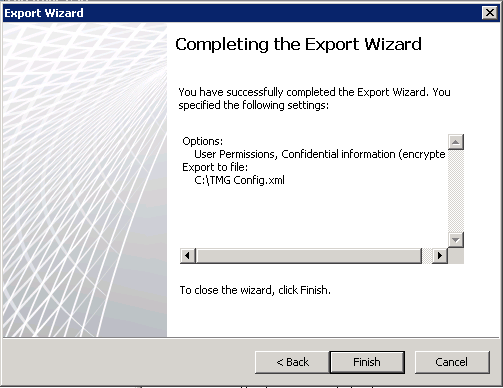
Copy the exported config file over to EMS01, log on to the server and open the TMG console.
Importing the TMG Array Configuration to the Enterprise Management Server
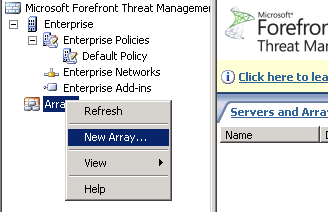
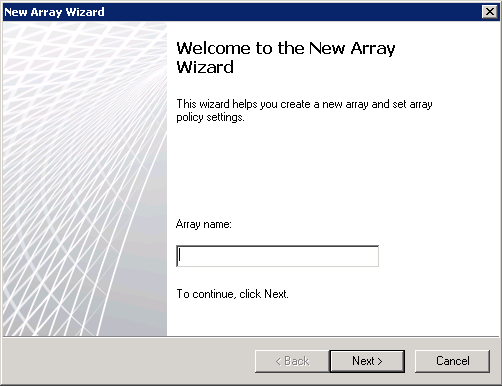
Right click Arrays and select “New Array…” and then match the array name exactly to the existing array
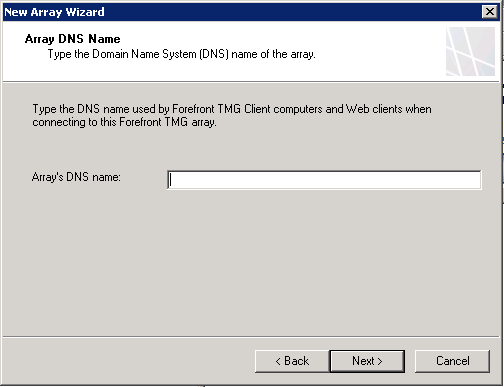
Match the Array DNS name exactly, and select the Default Policy
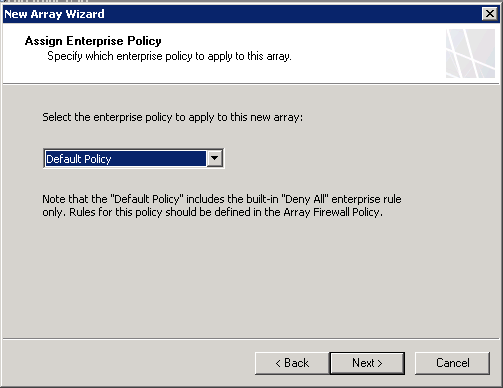
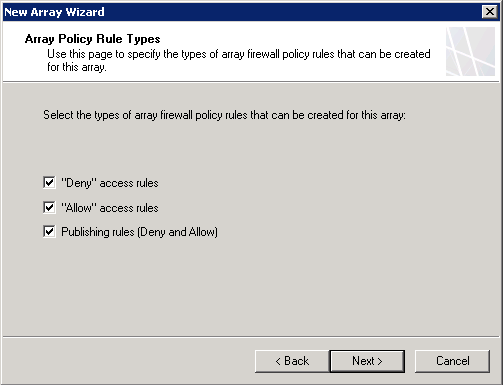
Ensure that all 3 policy types are checked and finish the wizard, but don’t apply the configuration yet! Right click on the array and select “Import (Restore)…”
Select the file we created before and select the option to “Overwrite (restore)”
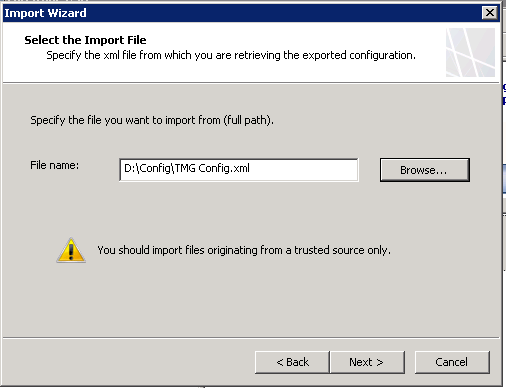
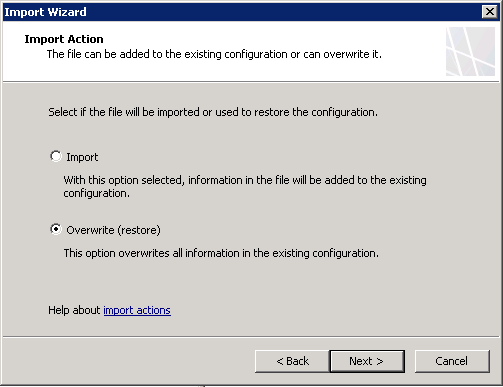
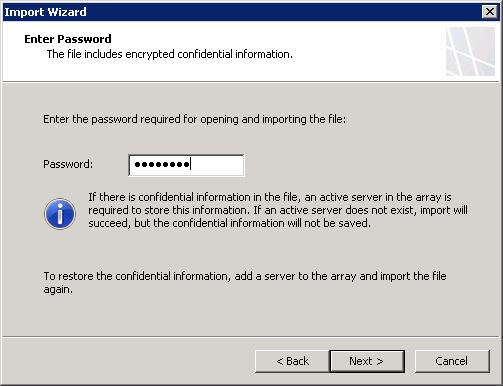
Select “Import server-specific information” and “Import user permission settings” and enter the password
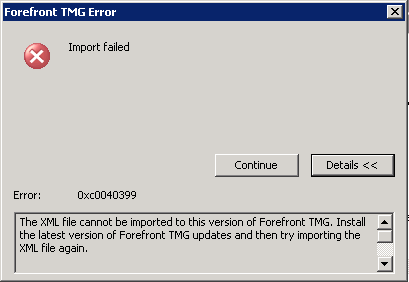
If you get the following error, ensure the EMS is at the same patch level as the array servers
Error 0xc0040399 - The XML file cannot be imported to this version of Forefront TMG. Install the latest version of Forefront TMG updates and then try importing the XML file again.
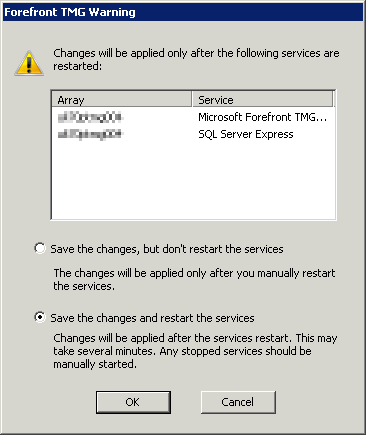
Once the import is completed, save the array configuration. You will be prompted to restart the services - select Save the changes and restart the services.
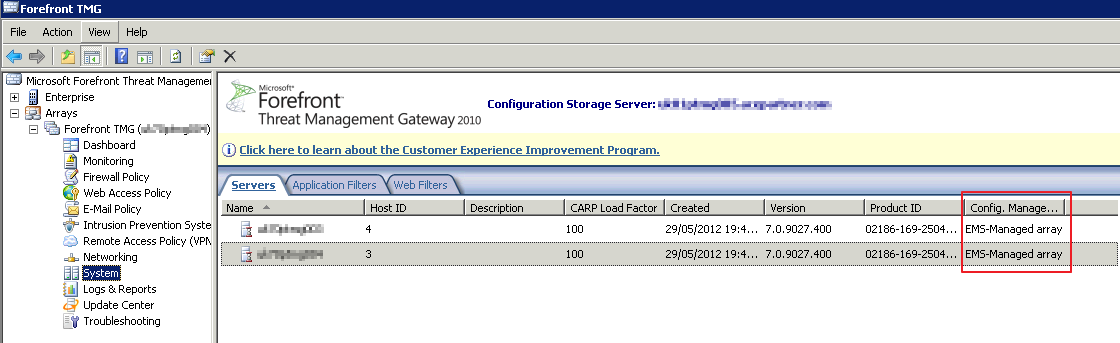
At this point the stand-alone array will not be affected - it’s still pointing at it’s own configuration storage on the array servers. If you look at the System tab, the connection to the servers will either have an hour glass, or a red cross - this is to be expected, they are not configured to talk to the EMS yet. The Config Management field will be set to “EMS-Managed Array”
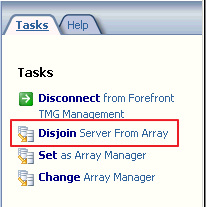
Disjoining Servers from the Stand-alone Array and joining the EMS Managed Array
Disjoining the servers will erase the config on the servers, so it needs to be done carefully and out of business hours. Disjoining the non-CSS server first will leave the current array manager in a working state while the other is disjoined and joined to the EMS. If you are using NLB, both servers will remain as part of the NLB while this happens - this can mean that traffic will be directed to the disjoined array but denied by the default rule.
Log directly onto the TMG server that is not the array manager, and open the TMG Console. Select the top node and in the actions pane, click the “Disjoin Server from Array” link.
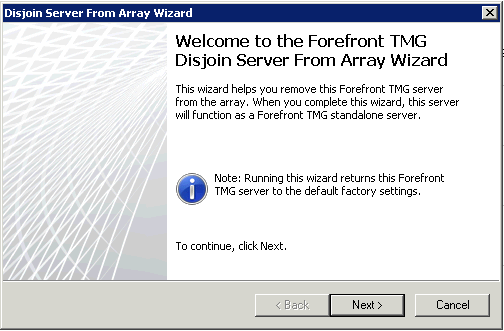
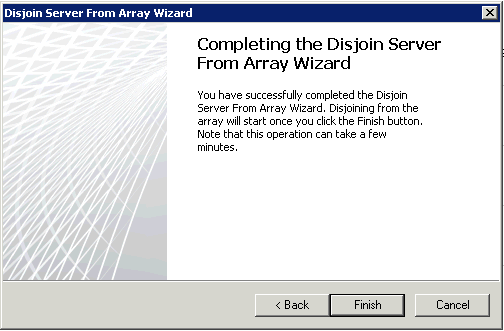
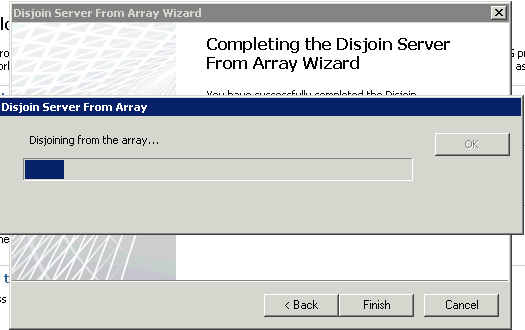
Now we have one of the array disjoined and ready to join the EMS managed array. Since the TMG config is essentially blank, create a rule to allow IPSEC again between the EMS and this server. Now run the “Join Array” wizard
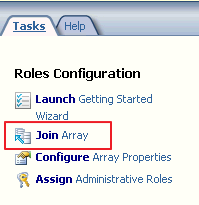
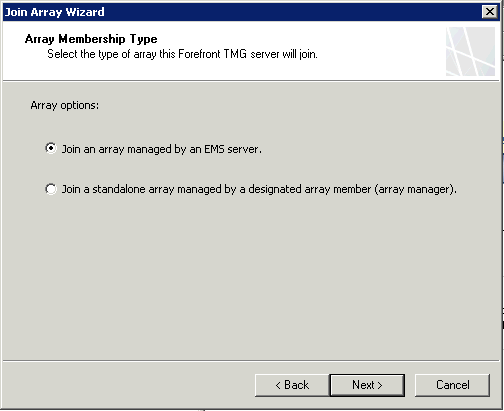
Enter the FQDN of the EMS and select the array you have just configured
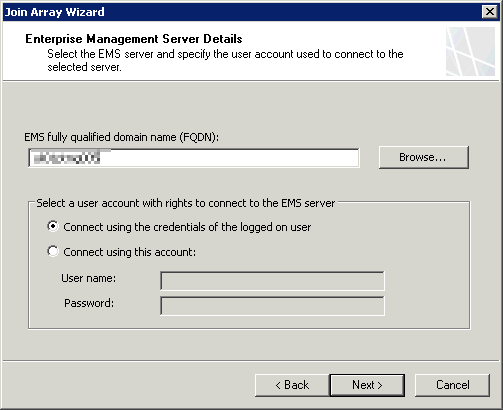
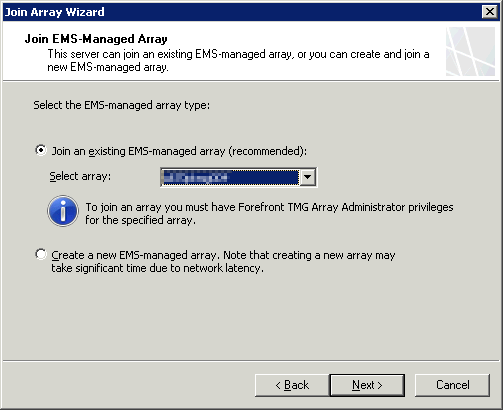
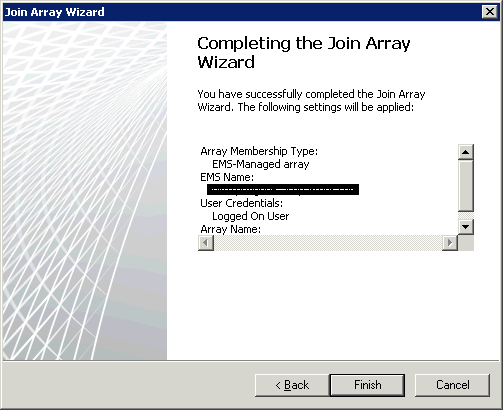
And that’s it - joined! Repeat the process for the other array member
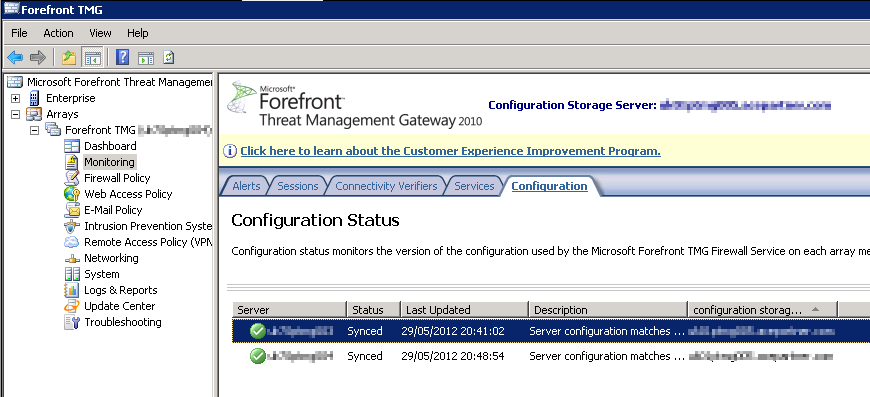
Check you have the servers correctly in the array, and the configuration is syncing correctly
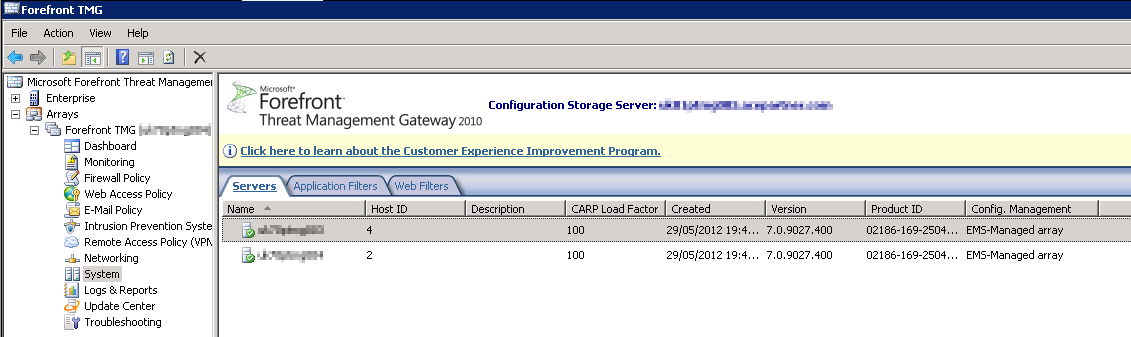
Since this post is getting long, I’ll split adding the 3rd server for another day - I’ll update here when it’s done.

 Written by
Written by