Configuring SSTP VPN connections to Threat Management Gateway 2010
 SSTP or SSL VPN connections are great for people working on client sites or behind very restrictive firewalls – they only require HTTPS (port 443) to be open to be able to connect. Unfortunately, you need to be running Windows 7 or Server 2008 (or newer) in order to make use of them. Threat Management Gateway 2010 is one option for an SSL VPN endpoint.
SSTP or SSL VPN connections are great for people working on client sites or behind very restrictive firewalls – they only require HTTPS (port 443) to be open to be able to connect. Unfortunately, you need to be running Windows 7 or Server 2008 (or newer) in order to make use of them. Threat Management Gateway 2010 is one option for an SSL VPN endpoint.
SSTP VPN Requirements
- Clients must be Windows 7/Server 2008 or newer
- Certificate – either commercial or an internal Certificate Authority
- Published CRL – SSTP clients check for the Certificate Revocation List of the CA
- If you already have an SSL listener (e.g. for Exchange publishing rules) then you need a dedicated IP address for the SSTP connection
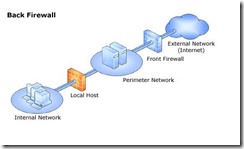
TMG is configured as a “back-firewall” in this environment, with an adaptor in the LAN and one in the Perimeter (DMZ). The DMZ has a NAT relationship to the External public IPs.
Requesting a Certificate from a Certificate Authority from Certificate Services 2003
Create a sstp.inf file to define the request. The subject CN MUST be the exact URL you’re going to use to access the SSL VPN, you can’t use a Subject Alternative Name (SAN):
Open a command prompt as administrator and generate a request file:
This generates a request file, which we’ll use to create the certificate on the Certificate Authority. Normally I would submit the request directly to the CA, but TMG does not play nicely with the RPC protocol, and I’ve not managed to get this working.
Copy the sstp.req file over to your CA and run another command prompt. Submit the request and save the response back to the TMG server:
This creates the certificate required for the SSL VPN, which you can then accept back on the TMG server:
If you need to, also install the CA’s Root Certificate in the Trusted Root Certification Authorities.
Configuring VPN Client Access
There are 6 steps in the Remote Access Policy (VPN) panel of the TMG console for setting up VPN connections, not all of them required.
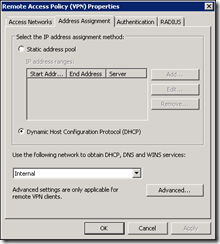
Configure Address Assignment Method and Enable VPN Client Access
So, click the first link and configure the Address Assignment. Since this TMG server has a leg in the LAN, it can use the DHCP server there, select the Internal Network. You can configure a static pool of IPs if you want – e.g. to put the clients on a more secure VLAN or to control access to resources based on a subnet:
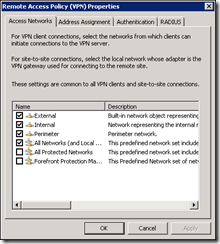
Select the Access Networks tab, and you can configure which networks the VPN clients can connect to. I’ve selected External and Perimeter for obivious reasons – that’s where my clients will be coming from. For testing purposes I’ve also selected the Internal network so I can test the SSL VPN from my desktop.
On the Authentication tab, select MS-CHAPv2 – this will allow the most secure username and password authentication method without issuing client certificates or smart cards (EAP). CHAP and PAP are basically a no-go.
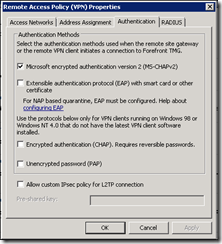
I haven’t configured a RADIUS server for this connection to keep it simple. The “Enable VPN Client Access” link will enable the System Policy firewall rule.
Specify Windows Users or select a RADIUS Server
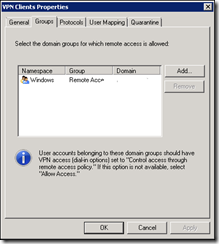
Click on the Specify Windows Users link and select a group from your Active Directory to allow VPN access.
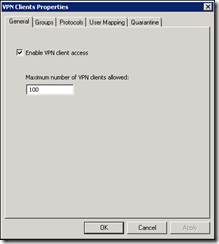
Under the General tab you can enable or disable VPN access and set a limit on the number of users allowed at the same time.
Under protocols, untick the Enable PPTP box and check the Enable SSTP
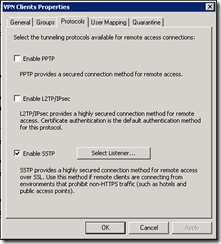
Click “Select Listener…” and create a New listener to open the Web Listener Wizard. Name the listener
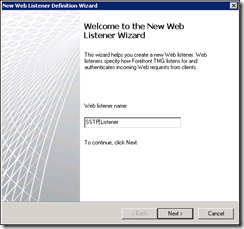
Select the Networks you want to configure the Listener for – the same as you configured for the Remote Access Policy is a good idea! To ensure that the SSL VPN has a unique certificate and IP address, specify the IP address you want the listener to listen on in the Perimeter network:
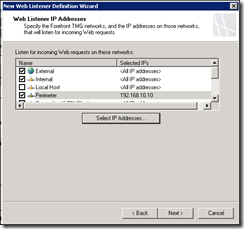
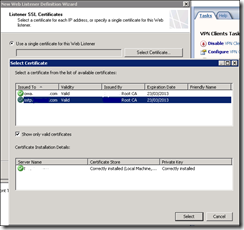
Select the Certificate you created earlier for the Listener and complete the wizard
Verify VPN Properties and Remote Access Configuration
Essentially, that means check what you’ve just done…not sure why this warrants a step MS?
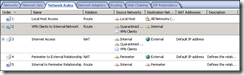
View Firewall Policy for the VPN Clients Network
Create a rule to control where you want your VPN Clients to access – for me the VPN clients are trusted and therefore I created a rule to allow “All outbound traffic” to “All Networks”:
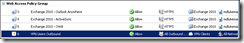
View Network Rules
Similarly, check that you’re happy with the Network Rules for the VPN clients – I didn’t need to change anything here.
Configure Quarantine (Optional)
As this is optional and I only want a simple setup so this will be a later post, hopefully!
Publishing your Certificate Revocation List
My CA is configured to add an external URL to the Certificates it creates – crl.definit.co.uk. This means that the CRL can be made publicly available, this is a requirement for SSTP clients which by default will check a certificate’s validity.
Using the Web Publishing Rule Wizard I created a rule called “CRL Publishing” to “allow” access to a single Web site or load balancer using HTTP connections to the internal site name and with a path of /CertEnroll/* on the Public name is the external URL – crl.definit.co.uk. I created a new HTTP only listener, set the rule to “No Authentication” and allowed “All users” access.
Configuring the SSTP client
Configuring the clients is very simple – on Windows 7 and Server 2008 it’s the same. First of all, ensure that you trust the certificate authority that issued the SSTP certificate created earlier, then open the “Set up a Connection or Network” wizard and select “Connect to a workplace”:
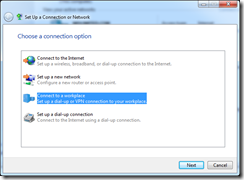
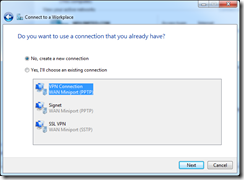
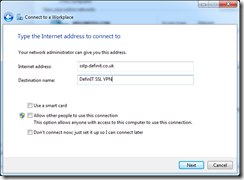
Connect via your internet connection and enter the url (sstp.definit.co.uk) and a nice name for it:
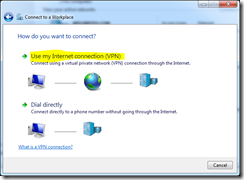
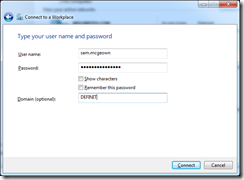
Enter your Active Directory User credentials (must be a member of the user group added earlier) and click “Connect”
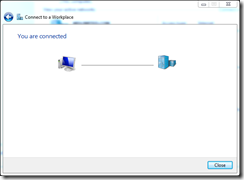
All being well, you’re connected! If you get errors, double check the certificates!

 Written by
Written by